ICTF 2023 - Idoriot Revenge
Idoriot Revenge
Idoriot Revenge is an easy web based challenge for ICTF2023. This ctf also had an Idoriot challenge before this. That solution was just an url traverse to the /flag.txt, this one was more fun.
The problem starts with only an url.
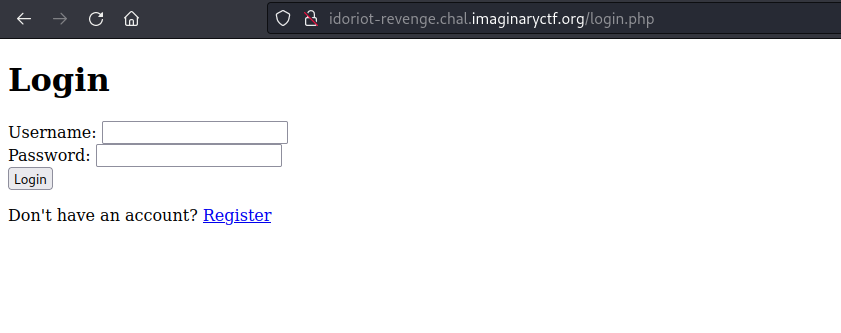
Login page is pretty basic. As well as a registration page link.
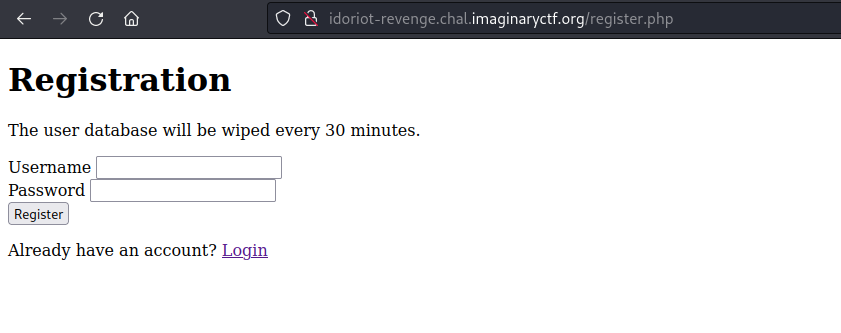
This page does state that the database is wiped every 30 minutes. Could wait until refresh and try to register a certain user like admin first. But, I started with a test account username and password.
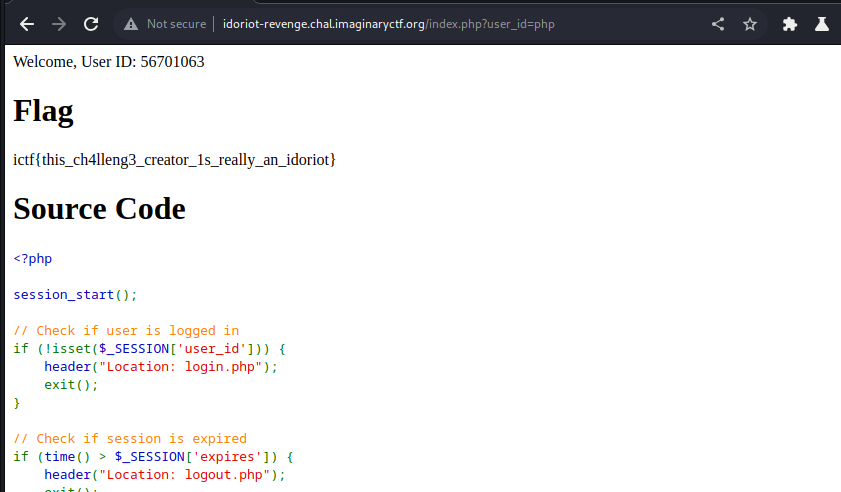
Once logged in the page is filled is filled with php code. Looks like the requirements for the flag are a userid of php and a username of admin. Userid is simple in the url can be changed.
For the admin login, I tried admin’1=1– as the username when registering. Since this is a sqlite database, I started to try sql injection usernames. This one worked.
After logging in as admin or admin’1=1–, I changed the user_id to php and got a flag.
This was a good beginner challenge. I like that you can use sql injection for the admin login. I’m sure there are other ways to login as admin, but this one worked for me.